- Home
- Mobiles
- Mobiles News
- Siri 'GoogolPlex' hack lets you voice control Web services, cars, and more
Siri 'GoogolPlex' hack lets you voice control Web services, cars, and more
By NDTV Correspondent | Updated: 18 April 2014 14:23 IST
Click Here to Add Gadgets360 As A Trusted Source

Advertisement
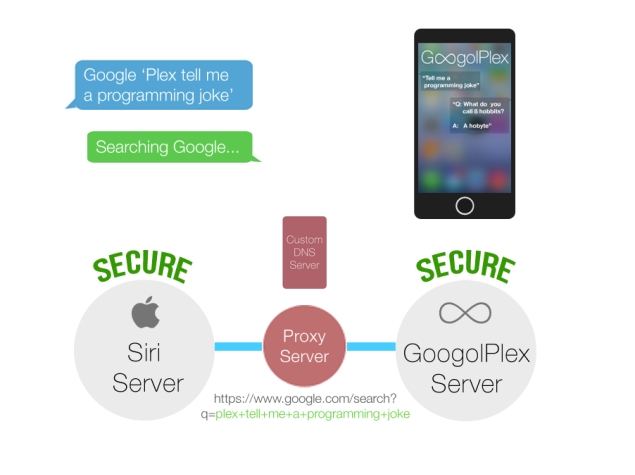
A team of four students at the University of Pennsylvania has created a hack for Siri, Apple's interactive voice assistant, that allows users to control home appliances, lighting, Web services, and even cars. The hack, called GoogolPlex, connects Siri to the programming interfaces supplied by third parties, via a simple Web proxy server.
Engadget reports that the four students - Alex Sands, Ajay Patel, Ben Hsu and Gagan Gupta - won third prize at the PenApps college hackathon for their idea. GoogolPlex is up and running, and anyone can check it out by pointing their iPhone or iPad to the team's proxy server through the device's Settings app.
By selecting the active Wi-Fi access point and changing the proxy to http://totally.betterthansiri.com, data is passed through the GoogolPlex project's servers. This allows the team to intercept a search term that is sent to Google after processing by Apple's massive data centers. The name "GoogolPlex" encourages commands to be sent to Google, as if users are specifically requesting a Web search.
GoogolPlex can currently interface with Spotify, Instagram, Philips Hue smart lighting products, Nest thermostats, and Tesla electric cars. Integration with an online payments service Venmo was also planned for demonstration purposes, but dropped.
Apple has so far restricted third parties from plugging in to Siri or creating extensions that would extend its functionality to more apps and services. GoogolPlex demonstrates what will be possible if and when Apple does decide to open Siri via APIs.
The student team has also published instructions for others to create their own commands by hooking into public APIs. User-created functions include asking Google Maps for directions, displaying a random XKCD comic, picking a random card from a deck, and flipping a coin.
Responses are understandably slow, as the popularity of GoogolPlex has spread. Some commands also require a helper app to be installed.
No jailbreaking or other modification is necessary, although rerouting all data through a third-party proxy does raise security implications as it can be intercepted, stored, or otherwise tampered with mid-stream.
The team hopes to continue working on GoogolPlex, and eventually develop a way to allow anyone to make custom commands work.
Engadget reports that the four students - Alex Sands, Ajay Patel, Ben Hsu and Gagan Gupta - won third prize at the PenApps college hackathon for their idea. GoogolPlex is up and running, and anyone can check it out by pointing their iPhone or iPad to the team's proxy server through the device's Settings app.
By selecting the active Wi-Fi access point and changing the proxy to http://totally.betterthansiri.com, data is passed through the GoogolPlex project's servers. This allows the team to intercept a search term that is sent to Google after processing by Apple's massive data centers. The name "GoogolPlex" encourages commands to be sent to Google, as if users are specifically requesting a Web search.
GoogolPlex can currently interface with Spotify, Instagram, Philips Hue smart lighting products, Nest thermostats, and Tesla electric cars. Integration with an online payments service Venmo was also planned for demonstration purposes, but dropped.
Apple has so far restricted third parties from plugging in to Siri or creating extensions that would extend its functionality to more apps and services. GoogolPlex demonstrates what will be possible if and when Apple does decide to open Siri via APIs.
The student team has also published instructions for others to create their own commands by hooking into public APIs. User-created functions include asking Google Maps for directions, displaying a random XKCD comic, picking a random card from a deck, and flipping a coin.
Responses are understandably slow, as the popularity of GoogolPlex has spread. Some commands also require a helper app to be installed.
No jailbreaking or other modification is necessary, although rerouting all data through a third-party proxy does raise security implications as it can be intercepted, stored, or otherwise tampered with mid-stream.
The team hopes to continue working on GoogolPlex, and eventually develop a way to allow anyone to make custom commands work.
Comments
Get your daily dose of tech news, reviews, and insights, in under 80 characters on Gadgets 360 Turbo. Connect with fellow tech lovers on our Forum. Follow us on X, Facebook, WhatsApp, Threads and Google News for instant updates. Catch all the action on our YouTube channel.
Further reading:
GoogolPlex, Siri, Siri extension, Siri hack, University of Pennsylvania, hackathon, iOS, voice automation, voice command
Popular on Gadgets
- Samsung Galaxy Unpacked 2025
- ChatGPT
- Redmi Note 14 Pro+
- iPhone 16
- Apple Vision Pro
- Oneplus 12
- OnePlus Nord CE 3 Lite 5G
- iPhone 13
- Xiaomi 14 Pro
- Oppo Find N3
- Tecno Spark Go (2023)
- Realme V30
- Best Phones Under 25000
- Samsung Galaxy S24 Series
- Cryptocurrency
- iQoo 12
- Samsung Galaxy S24 Ultra
- Giottus
- Samsung Galaxy Z Flip 5
- Apple 'Scary Fast'
- Housefull 5
- GoPro Hero 12 Black Review
- Invincible Season 2
- JioGlass
- HD Ready TV
- Laptop Under 50000
- Smartwatch Under 10000
- Latest Mobile Phones
- Compare Phones
Latest Gadgets
- OPPO A6v 5G
- OPPO A6i+ 5G
- Realme 16 5G
- Redmi Turbo 5
- Redmi Turbo 5 Max
- Moto G77
- Moto G67
- Realme P4 Power 5G
- HP HyperX Omen 15
- Acer Chromebook 311 (2026)
- Lenovo Idea Tab Plus
- Realme Pad 3
- HMD Watch P1
- HMD Watch X1
- Haier H5E Series
- Acerpure Nitro Z Series 100-inch QLED TV
- Asus ROG Ally
- Nintendo Switch Lite
- Haier 1.6 Ton 5 Star Inverter Split AC (HSU19G-MZAID5BN-INV)
- Haier 1.6 Ton 5 Star Inverter Split AC (HSU19G-MZAIM5BN-INV)
© Copyright Red Pixels Ventures Limited 2026. All rights reserved.












