- Home
- Mobiles
- Mobiles News
- iOS Flaw Could Allow Attackers to Steal iCloud Passwords and Sensitive Information
iOS Flaw Could Allow Attackers to Steal iCloud Passwords and Sensitive Information
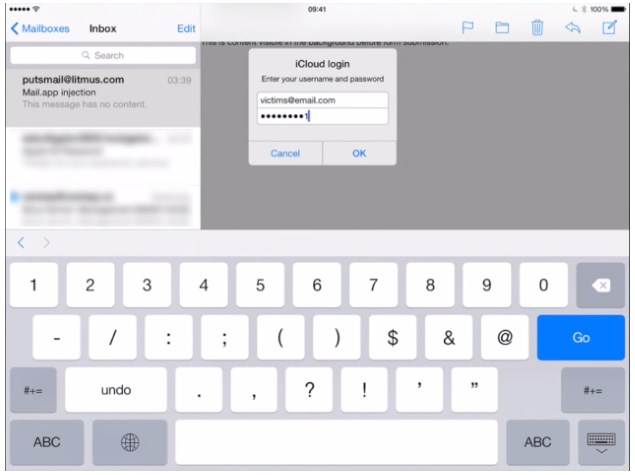
As Ars Technica reports, the flaw relates to Mail.app not properly stripping HTML code from the bodies of emails as they are displayed. One tag in particular, , instructs Mail.app to download and execute remote code. This can be exploited in a number of ways, one of which is to download a form which could look like an iCloud password prompt. If a user believes it is genuine, he or she would wind up sending his or her credentials to the attacker.
The proof-of-concept hack is sophisticated in that it uses the fact that downloaded code will only be displayed in Mail.app and not in any other client. iOS users will be presented with a dialog box that closely mimics the standard Apple ID prompt, and specifically asks for iCloud credentials.
Further, the flaw allows a tracking cookie to be set which prevents the code from being executed each time the same message is opened, to alleviate suspicion. If needed, the attacker can alter the code later so that different messages are displayed in order to steal different kinds of information.
Commentators on Github and various news outlets have pointed out that it is possible for users to realise that the dialog is not a genuine Apple prompt: it is not truly modal, which means the background will not fade out and other elements on screen will remain active. The fake input box prompts the user to input an ID as well as password, whereas standard Apple ID checks display the username already and ask only for the password. The keyboard is automatically displayed for genuine prompts, whereas you have to tap the fake one and it will move upwards when the keyboard pops up. Third-party keyboards and autocorrect are disabled for password entry, but the fake dialog box will not trigger any of those behaviours.
However, these are all subtle cues and many users could still very easily fall for the fake password prompt. It should also be noted that the flaw can be used to steal all kinds of information, and that the dialog shown need not necessarily be styled as a part of the iOS interface. iPhone and iPad users should be warned, as the code to enable such a hack is now freely available online and others are bound to come up with variations of their own.
Get your daily dose of tech news, reviews, and insights, in under 80 characters on Gadgets 360 Turbo. Connect with fellow tech lovers on our Forum. Follow us on X, Facebook, WhatsApp, Threads and Google News for instant updates. Catch all the action on our YouTube channel.
Related Stories
- Samsung Galaxy Unpacked 2026
- iPhone 17 Pro Max
- ChatGPT
- iOS 26
- Laptop Under 50000
- Smartwatch Under 10000
- Apple Vision Pro
- Oneplus 12
- OnePlus Nord CE 3 Lite 5G
- iPhone 13
- Xiaomi 14 Pro
- Oppo Find N3
- Tecno Spark Go (2023)
- Realme V30
- Best Phones Under 25000
- Samsung Galaxy S24 Series
- Cryptocurrency
- iQoo 12
- Samsung Galaxy S24 Ultra
- Giottus
- Samsung Galaxy Z Flip 5
- Apple 'Scary Fast'
- Housefull 5
- GoPro Hero 12 Black Review
- Invincible Season 2
- JioGlass
- HD Ready TV
- Latest Mobile Phones
- Compare Phones
- Realme C83 5G
- Nothing Phone 4a Pro
- Infinix Note 60 Ultra
- Nothing Phone 4a
- Honor 600 Lite
- Nubia Neo 5 GT
- Realme Narzo Power 5G
- Vivo X300 FE
- MacBook Neo
- MacBook Pro 16-Inch (M5 Max, 2026)
- Tecno Megapad 2
- Apple iPad Air 13-Inch (2026) Wi-Fi + Cellular
- Tecno Watch GT 1S
- Huawei Watch GT Runner 2
- Xiaomi QLED TV X Pro 75
- Haier H5E Series
- Asus ROG Ally
- Nintendo Switch Lite
- Haier 1.6 Ton 5 Star Inverter Split AC (HSU19G-MZAID5BN-INV)
- Haier 1.6 Ton 5 Star Inverter Split AC (HSU19G-MZAIM5BN-INV)

















