- Home
- Mobiles
- Mobiles News
- Google patches Android flaw that allows phishing apps to spoof genuine ones
Google patches Android flaw that allows phishing apps to spoof genuine ones
By NDTV Correspondent | Updated: 16 April 2014 14:17 IST
Click Here to Add Gadgets360 As A Trusted Source

Advertisement
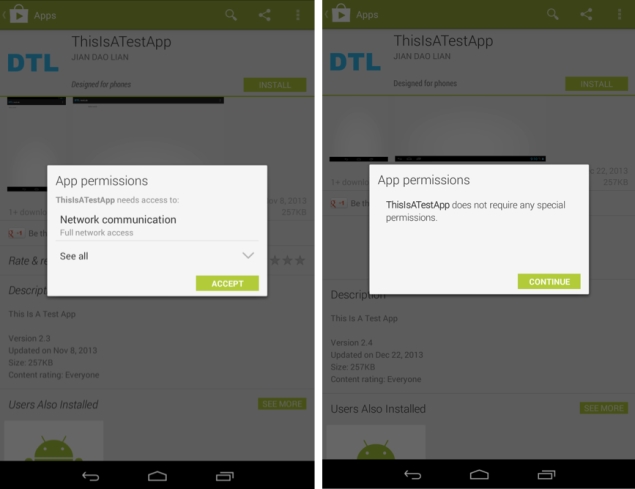
Google has released a patch that fixes a security vulnerability in Android related to app permissions. Security firm FireEye discovered late last year that apps could modify the icons of other apps on Android home screens and make them point to any other app or website, which would allow attackers to divert users to fake versions of trusted apps and websites in order to steal information.
The security lapse is possible because until now, apps have been able to modify the Android launcher's Read and Write attributes without explicitly asking for user permission. These permissions had previously been classified as "normal", indicating there was no known potential for abuse. "Normal" permissions are not displayed to the user prior to app installation, unlike more sensitive ones such as allowing access to location data, contacts, and the camera.
However, attackers could easily modify icons to point to malicious websites or apps that spoof the interfaces of known, trusted ones, such as banking and shopping apps. Commonly known as phishing, this kind of malware tricks users into entering their PIN numbers, passwords or credit card information, which are then stolen.
The problem affects devices up to and including those running Android 4.4.2, the most recent version. Custom Android skins including those of Samsung and HTC, as well as the aftermarket CyanogenMod, were found to be vulnerable.
FireEye demonstrated a proof of concept app which made it past Google's security scans and was briefly live in the Google Play store, but was withdrawn before anyone could accidentally download it. No requests for permissions were displayed to test users on a Nexus 7 tablet.
Google has now acknowledged the problem and has released a patch to Android device manufacturers, but it will be up to them to decide which devices will receive updates, and when. Android fragmentation is a known problem, and many devices might never be updated. Users must therefore be constantly vigilant of potential phishing attacks.
The security lapse is possible because until now, apps have been able to modify the Android launcher's Read and Write attributes without explicitly asking for user permission. These permissions had previously been classified as "normal", indicating there was no known potential for abuse. "Normal" permissions are not displayed to the user prior to app installation, unlike more sensitive ones such as allowing access to location data, contacts, and the camera.
However, attackers could easily modify icons to point to malicious websites or apps that spoof the interfaces of known, trusted ones, such as banking and shopping apps. Commonly known as phishing, this kind of malware tricks users into entering their PIN numbers, passwords or credit card information, which are then stolen.
The problem affects devices up to and including those running Android 4.4.2, the most recent version. Custom Android skins including those of Samsung and HTC, as well as the aftermarket CyanogenMod, were found to be vulnerable.
FireEye demonstrated a proof of concept app which made it past Google's security scans and was briefly live in the Google Play store, but was withdrawn before anyone could accidentally download it. No requests for permissions were displayed to test users on a Nexus 7 tablet.
Google has now acknowledged the problem and has released a patch to Android device manufacturers, but it will be up to them to decide which devices will receive updates, and when. Android fragmentation is a known problem, and many devices might never be updated. Users must therefore be constantly vigilant of potential phishing attacks.
Comments
Catch the latest from the Consumer Electronics Show on Gadgets 360, at our CES 2026 hub.
Related Stories
Popular on Gadgets
- Samsung Galaxy Unpacked 2025
- ChatGPT
- Redmi Note 14 Pro+
- iPhone 16
- Apple Vision Pro
- Oneplus 12
- OnePlus Nord CE 3 Lite 5G
- iPhone 13
- Xiaomi 14 Pro
- Oppo Find N3
- Tecno Spark Go (2023)
- Realme V30
- Best Phones Under 25000
- Samsung Galaxy S24 Series
- Cryptocurrency
- iQoo 12
- Samsung Galaxy S24 Ultra
- Giottus
- Samsung Galaxy Z Flip 5
- Apple 'Scary Fast'
- Housefull 5
- GoPro Hero 12 Black Review
- Invincible Season 2
- JioGlass
- HD Ready TV
- Laptop Under 50000
- Smartwatch Under 10000
- Latest Mobile Phones
- Compare Phones
Latest Gadgets
- Samsung Galaxy A07 5G
- Vivo Y500i
- OnePlus Turbo 6V
- OnePlus Turbo 6
- Itel Zeno 20 Max
- OPPO Reno 15 Pro Mini 5G
- Poco M8 Pro 5G
- Motorola Signature
- Lenovo Yoga Slim 7x (2025)
- Lenovo Yoga Slim 7a
- Realme Pad 3
- OPPO Pad Air 5
- NoiseFit Pro 6R
- Xiaomi Watch 5
- Acerpure Nitro Z Series 100-inch QLED TV
- Samsung 43 Inch LED Ultra HD (4K) Smart TV (UA43UE81AFULXL)
- Asus ROG Ally
- Nintendo Switch Lite
- Haier 1.6 Ton 5 Star Inverter Split AC (HSU19G-MZAID5BN-INV)
- Haier 1.6 Ton 5 Star Inverter Split AC (HSU19G-MZAIM5BN-INV)
© Copyright Red Pixels Ventures Limited 2026. All rights reserved.

















