- Home
- Mobiles
- Mobiles News
- Android Browser Security Hole Affects Millions of Users, Says Expert
Android Browser Security Hole Affects Millions of Users, Says Expert
By NDTV Correspondent | Updated: 16 September 2014 12:12 IST
Click Here to Add Gadgets360 As A Trusted Source

Advertisement
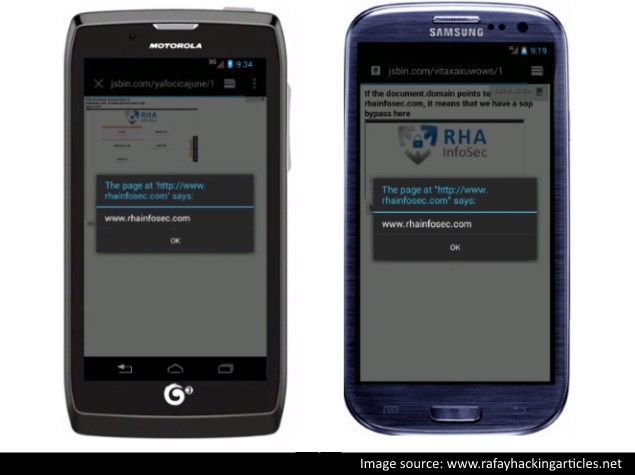
A massive security vulnerability has been discovered in all versions of the default Android browser, which is in use on millions of devices around the world. The flaw allows attackers to run scripts that can read the contents of any open tab, including things such as cookies and credentials that might let them harvest private data even later.
Users of devices running any version of Android prior to 4.4 with the standard browser are affected. According to Google's own analytics, quoted by Android Central and security community website SecurityStreet, this affects at least 75 percent of all Android users. A very large proportion of new phones also ship with Android 4.3 or lower.
The flaw was first publicised by ethical hacker and blogger Rafay Baloch, who has since tested it on a variety of devices. His findings have further been confirmed by others in the security industry. A module that exploits this flaw is also now widely available for the Metasploit penetration testing framework.
The problem relates to the inability of the Android (AOSP) browser to uphold a fundamental assumption, which is that websites which are open should be able to execute scripts, but those should not be able to affect the contents of any other open websites. The concept, known as Single-Origin Policy, can be bypassed for the Android browser by deliberately feeding it a malformed instruction which allows scripts to be run without supervision. The relatively simple exploit thus allows attackers to read data even from secure sites once they are opened, and redirect the data to wherever they want.
Google has not yet responded to the disclosure. The Android browser was officially deprecated in favour of Chrome with Android 4.4. A huge number of devices currently in use will never be updated to 4.4, including many low-priced ones that are being sold as new today.
Users of devices running any version of Android prior to 4.4 with the standard browser are affected. According to Google's own analytics, quoted by Android Central and security community website SecurityStreet, this affects at least 75 percent of all Android users. A very large proportion of new phones also ship with Android 4.3 or lower.
The flaw was first publicised by ethical hacker and blogger Rafay Baloch, who has since tested it on a variety of devices. His findings have further been confirmed by others in the security industry. A module that exploits this flaw is also now widely available for the Metasploit penetration testing framework.
The problem relates to the inability of the Android (AOSP) browser to uphold a fundamental assumption, which is that websites which are open should be able to execute scripts, but those should not be able to affect the contents of any other open websites. The concept, known as Single-Origin Policy, can be bypassed for the Android browser by deliberately feeding it a malformed instruction which allows scripts to be run without supervision. The relatively simple exploit thus allows attackers to read data even from secure sites once they are opened, and redirect the data to wherever they want.
Google has not yet responded to the disclosure. The Android browser was officially deprecated in favour of Chrome with Android 4.4. A huge number of devices currently in use will never be updated to 4.4, including many low-priced ones that are being sold as new today.
Comments
Get your daily dose of tech news, reviews, and insights, in under 80 characters on Gadgets 360 Turbo. Connect with fellow tech lovers on our Forum. Follow us on X, Facebook, WhatsApp, Threads and Google News for instant updates. Catch all the action on our YouTube channel.
Related Stories
Popular on Gadgets
- Samsung Galaxy Unpacked 2026
- iPhone 17 Pro Max
- ChatGPT
- iOS 26
- Laptop Under 50000
- Smartwatch Under 10000
- Apple Vision Pro
- Oneplus 12
- OnePlus Nord CE 3 Lite 5G
- iPhone 13
- Xiaomi 14 Pro
- Oppo Find N3
- Tecno Spark Go (2023)
- Realme V30
- Best Phones Under 25000
- Samsung Galaxy S24 Series
- Cryptocurrency
- iQoo 12
- Samsung Galaxy S24 Ultra
- Giottus
- Samsung Galaxy Z Flip 5
- Apple 'Scary Fast'
- Housefull 5
- GoPro Hero 12 Black Review
- Invincible Season 2
- JioGlass
- HD Ready TV
- Latest Mobile Phones
- Compare Phones
Latest Gadgets
- Realme C83 5G
- Nothing Phone 4a Pro
- Infinix Note 60 Ultra
- Nothing Phone 4a
- Honor 600 Lite
- Nubia Neo 5 GT
- Realme Narzo Power 5G
- Vivo X300 FE
- MacBook Neo
- MacBook Pro 16-Inch (M5 Max, 2026)
- Tecno Megapad 2
- Apple iPad Air 13-Inch (2026) Wi-Fi + Cellular
- Tecno Watch GT 1S
- Huawei Watch GT Runner 2
- Xiaomi QLED TV X Pro 75
- Haier H5E Series
- Asus ROG Ally
- Nintendo Switch Lite
- Haier 1.6 Ton 5 Star Inverter Split AC (HSU19G-MZAID5BN-INV)
- Haier 1.6 Ton 5 Star Inverter Split AC (HSU19G-MZAIM5BN-INV)
© Copyright Red Pixels Ventures Limited 2026. All rights reserved.
















