- Home
- Laptops
- Laptops News
- OS X Yosemite v10.10.2 Now Available for Download
OS X Yosemite v10.10.2 Now Available for Download
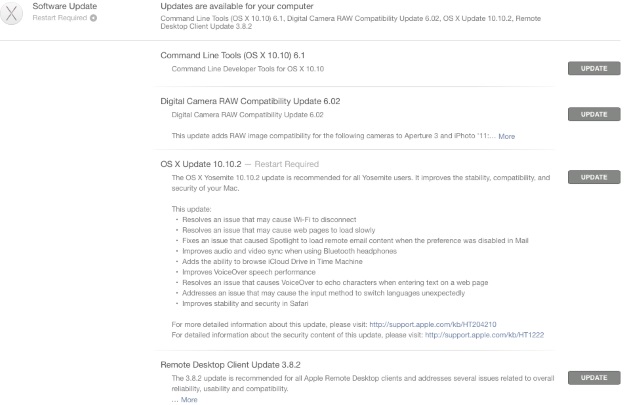
OS X Yosemite v10.10.2 brings fix for an issue that might cause Wi-Fi to disconnect, while resolving another issue that might cause Web pages to load slowly. The update also claims to fix an issue that could cause Spotlight to load remote email content when this preference is disabled in Mail, a problem that had raised some privacy concerns recently. The update also brings other fixes and enhancements detailed below.
You can install the update by going to the Updates tab of the Mac App Store. We recommend backing up your Mac using Time Machine or any other application before installing any system update.
Here are the release notes of the OS X Yosemite v10.10.2 update in full:
This update includes the following improvements:
- Resolves an issue that might cause Wi-Fi to disconnect
- Resolves an issue that might cause web pages to load slowly
- Fixes an issue that could cause Spotlight to load remote email content when this preference is disabled in Mail
- Improves audio and video sync when using Bluetooth headphones
- Adds the ability to browse iCloud Drive in Time Machine
- Improves VoiceOver speech performance
- Resolves an issue that could cause VoiceOver to echo characters when entering text on a web page
- Addresses an issue that could cause the input method to switch languages unexpectedly
- Improves stability and security in Safari
Enterprise content
For enterprise customers, this update:
- Improves performance for browsing DFS shares in the Finder
- Fixes an issue where certain Calendar invitations could be displayed at the incorrect time
- Fixes an issue for Microsoft Exchange accounts where the organizer of a meeting might not be notified when someone accepts an invitation using Calendar
- Addresses an issue where Safari could continually prompt for credentials when accessing a site protected by NTLM authentication
- Adds the ability to set "Out of Office" reply dates for Microsoft Exchange accounts in Mail
Security Content
- AFP Server
Available for: OS X Mavericks v10.9.5
Impact: A remote attacker may be able to determine all the network addresses of the system
Description: The AFP file server supported a command which returned all the network addresses of the system. This issue was addressed by removing the addresses from the result.
CVE-ID
CVE-2014-4426 : Craig Young of Tripwire VERT
- bash
Available for: OS X Yosemite v10.10 and v10.10.1
Impact: Multiple vulnerabilities in bash, including one that may allow local attackers to execute arbitrary code
Description: Multiple vulnerabilities existed in bash. These issues were addressed by updating bash to patch level 57.
CVE-ID
CVE-2014-6277
CVE-2014-7186
CVE-2014-7187
- Bluetooth
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5
Impact: A malicious application may be able to execute arbitrary code with system privileges
Description: An integer signedness error existed in IOBluetoothFamily which allowed manipulation of kernel memory. This issue was addressed through improved bounds checking. This issue does not affect OS X Yosemite systems.
CVE-ID
CVE-2014-4497
- Bluetooth
Available for: OS X Yosemite v10.10 and v10.10.1
Impact: A malicious application may be able to execute arbitrary code with system privileges
Description: An error existed in the Bluetooth driver that allowed a malicious application to control the size of a write to kernel memory. The issue was addressed through additional input validation.
CVE-ID
CVE-2014-8836 : Ian Beer of Google Project Zero
- Bluetooth
Available for: OS X Yosemite v10.10 and v10.10.1
Impact: A malicious application may be able to execute arbitrary code with system privileges
Description: Multiple security issues existed in the Bluetooth driver, allowing a malicious application to execute arbitrary code with system privilege. The issues were addressed through additional input validation.
CVE-ID
CVE-2014-8837 : Roberto Paleari and Aristide Fattori of Emaze Networks
- CFNetwork Cache
Available for: OS X Yosemite v10.10 and v10.10.1
Impact: Website cache may not be fully cleared after leaving private browsing
Description: A privacy issue existed where browsing data could remain in the cache after leaving private browsing. This issue was addressed through a change in caching behavior.
CVE-ID
CVE-2014-4460
- CoreGraphics
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: Opening a maliciously crafted PDF file may lead to an unexpected application termination or arbitrary code execution
Description: An integer overflow existed in the handling of PDF files. This issue was addressed through improved bounds checking.
CVE-ID
CVE-2014-4481 : Felipe Andres Manzano of the Binamuse VRT, via the iSIGHT Partners GVP Program
- CPU Software
Available for: OS X Yosemite v10.10 and v10.10.1, for: MacBook Pro Retina, MacBook Air (Mid 2013 and later), iMac (Late 2013 and later), Mac Pro (Late 2013)
Impact: A malicious Thunderbolt device may be able to affect firmware flashing
Description: Thunderbolt devices could modify the host firmware if connected during an EFI update. This issue was addressed by not loading option ROMs during updates.
CVE-ID
CVE-2014-4498 : Trammell Hudson of Two Sigma Investments
- CommerceKit Framework
Available for: OS X Yosemite v10.10 and v10.10.1
Impact: An attacker with access to a system may be able to recover Apple ID credentials
Description: An issue existed in the handling of App Store logs. The App Store process could log Apple ID credentials in the log when additional logging was enabled. This issue was addressed by disallowing logging of credentials.
CVE-ID
CVE-2014-4499 : Sten Petersen
- CoreGraphics
Available for: OS X Yosemite v10.10 and v10.10.1
Impact: Some third-party applications with non-secure text entry and mouse events may log those events
Description: Due to the combination of an uninitialized variable and an application's custom allocator, non-secure text entry and mouse events may have been logged. This issue was addressed by ensuring that logging is off by default. This issue did not affect systems prior to OS X Yosemite.
CVE-ID
CVE-2014-1595 : Steven Michaud of Mozilla working with Kent Howard
- CoreGraphics
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5
Impact: Opening a maliciously crafted PDF file may lead to an unexpected application termination or arbitrary code execution
Description: A memory corruption issue existed in the handling of PDF files. The issue was addressed through improved bounds checking. This issue does not affect OS X Yosemite systems.
CVE-ID
CVE-2014-8816 : Mike Myers, of Digital Operatives LLC
- CoreSymbolication
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: A malicious application may be able to execute arbitrary code with system privileges
Description: Multiple type confusion issues existed in coresymbolicationd's handling of XPC messages. These issues were addressed through improved type checking.
CVE-ID
CVE-2014-8817 : Ian Beer of Google Project Zero
- FontParser
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: Processing a maliciously crafted .dfont file may lead to an unexpected application termination or arbitrary code execution
Description: A memory corruption issue existed in the handling of .dfont files. This issue was addressed through improved bounds checking.
CVE-ID
CVE-2014-4484 : Gaurav Baruah working with HP's Zero Day Initiative
- FontParser
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: Opening a maliciously crafted PDF file may lead to an unexpected application termination or arbitrary code execution
Description: A buffer overflow existed in the handling of font files. This issue was addressed through improved bounds checking.
CVE-ID
CVE-2014-4483 : Apple
- Foundation
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: Viewing a maliciously crafted XML file may lead to an unexpected application termination or arbitrary code execution
Description: A buffer overflow existed in the XML parser. This issue was addressed through improved bounds checking.
CVE-ID
CVE-2014-4485 : Apple
- Intel Graphics Driver
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: Multiple vulnerabilities in Intel graphics driver
Description: Multiple vulnerabilities existed in the Intel graphics driver, the most serious of which may have led to arbitrary code execution with system privileges. This update addresses the issues through additional bounds checks.
CVE-ID
CVE-2014-8819 : Ian Beer of Google Project Zero
CVE-2014-8820 : Ian Beer of Google Project Zero
CVE-2014-8821 : Ian Beer of Google Project Zero
- IOAcceleratorFamily
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: A malicious application may be able to execute arbitrary code with system privileges
Description: A null pointer dereference existed in IOAcceleratorFamily's handling of certain IOService userclient types. This issue was addressed through improved validation of IOAcceleratorFamily contexts.
CVE-ID
CVE-2014-4486 : Ian Beer of Google Project Zero
- IOHIDFamily
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: A malicious application may be able to execute arbitrary code with system privileges
Description: A buffer overflow existed in IOHIDFamily. This issue was addressed with improved bounds checking.
CVE-ID
CVE-2014-4487 : TaiG Jailbreak Team
- IOHIDFamily
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: A malicious application may be able to execute arbitrary code with system privileges
Description: A validation issue existed in IOHIDFamily's handling of resource queue metadata. This issue was addressed through improved validation of metadata.
CVE-ID
CVE-2014-4488 : Apple
- IOHIDFamily
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: A malicious application may be able to execute arbitrary code with system privileges
Description: A null pointer dereference existed in IOHIDFamily's handling of event queues. This issue was addressed through improved validation of IOHIDFamily event queue initialization.
CVE-ID
CVE-2014-4489 : @beist
- IOHIDFamily
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: Executing a malicious application may result in arbitrary code execution within the kernel
Description: A bounds checking issue existed in a user client vended by the IOHIDFamily driver which allowed a malicious application to overwrite arbitrary portions of the kernel address space. The issue is addressed by removing the vulnerable user client method.
CVE-ID
CVE-2014-8822 : Vitaliy Toropov working with HP's Zero Day Initiative
- IOKit
Available for: OS X Yosemite v10.10 and v10.10.1
Impact: A malicious application may be able to execute arbitrary code with system privileges
Description: An integer overflow existed in the handling of IOKit functions. This issue was addressed through improved validation of IOKit API arguments.
CVE-ID
CVE-2014-4389 : Ian Beer of Google Project Zero
- IOUSBFamily
Available for: OS X Yosemite v10.10 and v10.10.1
Impact: A privileged application may be able to read arbitrary data from kernel memory
Description: A memory access issue existed in the handling of IOUSB controller user client functions. This issue was addressed through improved argument validation.
CVE-ID
CVE-2014-8823 : Ian Beer of Google Project Zero
- Kernel
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: A malicious application may be able to execute arbitrary code with system privileges
Description: Specifying a custom cache mode allowed writing to kernel read-only shared memory segments. This issue was addressed by not granting write permissions as a side-effect of some custom cache modes.
CVE-ID
CVE-2014-4495 : Ian Beer of Google Project Zero
- Kernel
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: A malicious application may be able to execute arbitrary code with system privileges
Description: A validation issue existed in the handling of certain metadata fields of IODataQueue objects. This issue was addressed through improved validation of metadata.
CVE-ID
CVE-2014-8824 : @PanguTeam
- Kernel
Available for: OS X Yosemite v10.10 and v10.10.1
Impact: A local attacker can spoof directory service responses to the kernel, elevate privileges, or gain kernel execution
Description: Issues existed in identitysvc validation of the directory service resolving process, flag handling, and error handling. This issue was addressed through improved validation.
CVE-ID
CVE-2014-8825 : Alex Radocea of CrowdStrike
- Kernel
Available for: OS X Yosemite v10.10 and v10.10.1
Impact: A local user may be able to determine kernel memory layout
Description: Multiple uninitialized memory issues existed in the network statistics interface, which led to the disclosure of kernel memory content. This issue was addressed through additional memory initialization.
CVE-ID
CVE-2014-4371 : Fermin J. Serna of the Google Security Team
CVE-2014-4419 : Fermin J. Serna of the Google Security Team
CVE-2014-4420 : Fermin J. Serna of the Google Security Team
CVE-2014-4421 : Fermin J. Serna of the Google Security Team
- Kernel
Available for: OS X Mavericks v10.9.5
Impact: A person with a privileged network position may cause a denial of service
Description: A race condition issue existed in the handling of IPv6 packets. This issue was addressed through improved lock state checking.
CVE-ID
CVE-2011-2391
- Kernel
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: Maliciously crafted or compromised applications may be able to determine addresses in the kernel
Description: An information disclosure issue existed in the handling of APIs related to kernel extensions. Responses containing an OSBundleMachOHeaders key may have included kernel addresses, which may aid in bypassing address space layout randomization protection. This issue was addressed by unsliding the addresses before returning them.
CVE-ID
CVE-2014-4491 : @PanguTeam, Stefan Esser
- Kernel
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: A malicious application may be able to execute arbitrary code with system privileges
Description: A validation issue existed in the handling of certain metadata fields of IOSharedDataQueue objects. This issue was addressed through relocation of the metadata.
CVE-ID
CVE-2014-4461 : @PanguTeam
- LaunchServices
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: A malicious JAR file may bypass Gatekeeper checks
Description: An issue existed in the handling of application launches which allowed certain malicious JAR files to bypass Gatekeeper checks. This issue was addressed through improved handling of file type metadata.
CVE-ID
CVE-2014-8826 : Hernan Ochoa of Amplia Security
- libnetcore
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: A malicious, sandboxed app can compromise the networkd daemon
Description: Multiple type confusion issues existed in networkd's handling of interprocess communication. By sending networkd a maliciously formatted message, it may have been possible to execute arbitrary code as the networkd process. The issue is addressed through additional type checking.
CVE-ID
CVE-2014-4492 : Ian Beer of Google Project Zero
- LoginWindow
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: A Mac may not lock immediately upon wake
Description: An issue existed in the rendering of the lock screen. This issue was address through improved screen rendering while locked.
CVE-ID
CVE-2014-8827 : Xavier Bertels of Mono, and multiple OS X seed testers
- lukemftp
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: Using the command line ftp tool to fetch files from a malicious http server may lead to arbitrary code execution
Description: A command injection issue existed in the handling of HTTP redirects. This issue was addressed through improved validation of special characters.
CVE-ID
CVE-2014-8517
- OpenSSL
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: Multiple vulnerabilities in OpenSSL 0.9.8za, including one that may allow an attacker to downgrade connections to use weaker cipher-suites in applications using the library
Description: Multiple vulnerabilities existed in OpenSSL 0.9.8za. These issues were addressed by updating OpenSSL to version 0.9.8zc.
CVE-ID
CVE-2014-3566
CVE-2014-3567
CVE-2014-3568
- Sandbox
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5
Impact: A sandboxed process may be able to circumvent sandbox restrictions
Description: A design issue existed in the caching of sandbox profiles which allowed sandboxed applications to gain write access to the cache. This issue was addressed by restricting write access to paths containing a "com.apple.sandbox" segment. This issue does not affect OS X Yosemite v10.10 or later.
CVE-ID
CVE-2014-8828 : Apple
- SceneKit
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5
Impact: A malicious application could execute arbitrary code leading to compromise of user information
Description: Multiple out of bounds write issues existed in SceneKit. These issues were addressed through improved bounds checking.
CVE-ID
CVE-2014-8829 : Jose Duart of the Google Security Team
- SceneKit
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: Viewing a maliciously crafted Collada file may lead to an unexpected application termination or arbitrary code execution
Description: A heap buffer overflow existed in SceneKit's handling of Collada files. Viewing a maliciously crafted Collada file may have led to an unexpected application termination or arbitrary code execution. This issue was addressed through improved validation of accessor elements.
CVE-ID
CVE-2014-8830 : Jose Duart of Google Security Team
- Security
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: A downloaded application signed with a revoked Developer ID certificate may pass Gatekeeper checks
Description: An issue existed with how cached application certificate information was evaluated. This issue was addressed with cache logic improvements.
CVE-ID
CVE-2014-8838 : Apple
- security_taskgate
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: An app may access keychain items belonging to other apps
Description: An access control issue existed in the Keychain. Applications signed with self-signed or Developer ID certificates could access keychain items whose access control lists were based on keychain groups. This issue was addressed by validating the signing identity when granting access to keychain groups.
CVE-ID
CVE-2014-8831 : Apple
- Spotlight
Available for: OS X Yosemite v10.10 and v10.10.1
Impact: The sender of an email could determine the IP address of the recipient
Description: Spotlight did not check the status of Mail's "Load remote content in messages" setting. This issue was addressed by improving configuration checking.
CVE-ID
CVE-2014-8839 : John Whitehead of The New York Times, Frode Moe of LastFriday.no
- Spotlight
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: Spotlight may save unexpected information to an external hard drive
Description: An issue existed in Spotlight where memory contents may have been written to external hard drives when indexing. This issue was addressed with better memory management.
CVE-ID
CVE-2014-8832 : F-Secure
- SpotlightIndex
Available for: OS X Yosemite v10.10 and v10.10.1
Impact: Spotlight may display results for files not belonging to the user
Description: A deserialization issue existed in Spotlight's handling of permission caches. A user performing a Spotlight query may have been shown search results referencing files for which they don't have sufficient privileges to read. This issue was addressed with improved bounds checking.
CVE-ID
CVE-2014-8833 : David J Peacock, Independent Technology Consultant
- sysmond
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10 and v10.10.1
Impact: A malicious application may be able to execute arbitrary code with root privileges
Description: A type confusion vulnerability existed in sysmond that allowed a local application to escalate privileges. The issue was addressed with improved type checking.
CVE-ID
CVE-2014-8835 : Ian Beer of Google Project Zero
- UserAccountUpdater
Available for: OS X Yosemite v10.10 and v10.10.1
Impact: Printing-related preference files may contain sensitive information about PDF documents
Description: OS X Yosemite v10.10 addressed an issue in the handling of password-protected PDF files created from the Print dialog where passwords may have been included in printing preference files. This update removes such extraneous information that may have been present in printing preference files.
CVE-ID
CVE-2014-8834 : Apple
- WebKit
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, OS X Yosemite v10.10.1
Impact: Visiting a maliciously crafted website may lead to an unexpected application termination or arbitrary code execution
Description: Multiple memory corruption issues existed in WebKit. These issues were addressed through improved memory handling.
CVE-ID
CVE-2014-3192 : cloudfuzzer
CVE-2014-4476 : Apple
CVE-2014-4477 : lokihardt@ASRT working with HP's Zero Day Initiative
CVE-2014-4479 : Apple
Get your daily dose of tech news, reviews, and insights, in under 80 characters on Gadgets 360 Turbo. Connect with fellow tech lovers on our Forum. Follow us on X, Facebook, WhatsApp, Threads and Google News for instant updates. Catch all the action on our YouTube channel.
Related Stories
- Samsung Galaxy Unpacked 2026
- iPhone 17 Pro Max
- ChatGPT
- iOS 26
- Laptop Under 50000
- Smartwatch Under 10000
- Apple Vision Pro
- Oneplus 12
- OnePlus Nord CE 3 Lite 5G
- iPhone 13
- Xiaomi 14 Pro
- Oppo Find N3
- Tecno Spark Go (2023)
- Realme V30
- Best Phones Under 25000
- Samsung Galaxy S24 Series
- Cryptocurrency
- iQoo 12
- Samsung Galaxy S24 Ultra
- Giottus
- Samsung Galaxy Z Flip 5
- Apple 'Scary Fast'
- Housefull 5
- GoPro Hero 12 Black Review
- Invincible Season 2
- JioGlass
- HD Ready TV
- Latest Mobile Phones
- Compare Phones
- Realme C83 5G
- Nothing Phone 4a Pro
- Infinix Note 60 Ultra
- Nothing Phone 4a
- Honor 600 Lite
- Nubia Neo 5 GT
- Realme Narzo Power 5G
- Vivo X300 FE
- MacBook Neo
- MacBook Pro 16-Inch (M5 Max, 2026)
- Tecno Megapad 2
- Apple iPad Air 13-Inch (2026) Wi-Fi + Cellular
- Tecno Watch GT 1S
- Huawei Watch GT Runner 2
- Xiaomi QLED TV X Pro 75
- Haier H5E Series
- Asus ROG Ally
- Nintendo Switch Lite
- Haier 1.6 Ton 5 Star Inverter Split AC (HSU19G-MZAID5BN-INV)
- Haier 1.6 Ton 5 Star Inverter Split AC (HSU19G-MZAIM5BN-INV)

















