- Home
- Internet
- Internet News
- Hacking Team Gets Hacked: 5 Revelations From the Data Breach
Hacking Team Gets Hacked: 5 Revelations From the Data Breach
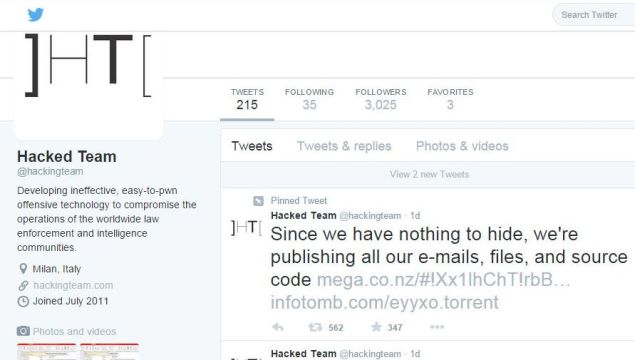
"Since we have nothing to hide, we're publishing all our emails, files and source code," says a deleted Twitter message, which included links to the torrent file. Hacking Team had lost control of its Twitter handle for over 12 hours, during which screenshots of internal emails were posted.
Phineas Fisher had previously hacked Gamma International, a British-German surveillance company that's behind the spyware software FinFisher. The hacker tweeted out screenshots of internal company emails in which competitors were discussed, and took credit for both the exploits on his Twitter handle.
gamma and HT down, a few more to go :)
-- Phineas Fisher (@GammaGroupPR) July 6, 2015
The torrent file is now being pored upon by numerous infosec experts, who are having a field day analysing the company's internal emails and its source code.
#HackerTeam's CEO on Ross Ulbricht:
"An EXEMPLARY punishment. This is JUST. This IS the
Justice we need"
HOORAY pic.twitter.com/vs6PrWcjB8
-- Moustache (@lamoustache) July 6, 2015
In this Twitter thread, hackers are debating whether the source code of their malware was used to plant child pornography on a victim's computer.
Nothing like planting evidence when your main customer is
law enforcement globally. #HackingTeam pic.twitter.com/XnYux3wEI0
-- Anis (@hertzmau5) July 6, 2015Hacking Team had a folder called "Anti HT Activists", which kept a log of research groups like Citizen Lab, a digital rights research group. Independent security researcher Claudio Guarnieri was quick to point this out after poring over their emails.
Interesting, we fall under the "Anti HT
activists" folder https://t.co/VK1qFurAt9
-- Claudio (@botherder) July 6, 2015Citizen Lab had previously reported on how Hacking Team software was used by governments to track journalists and dissidents in Africa and the Middle East. Hacking Team's clients list includes Russia and Sudan, which are 'not offically supported'.
#HackingTeam European clients: Czech R, Cyprus, Poland, Spain, Hungary, Luxembourg #ppint http://t.co/zSnPTlZLs2 pic.twitter.com/uHPPMzAAvB
-- OXI Angela (@Miss_Cybernaut) July 6, 2015when #HACKINGTEAM claimed Sudan & Russia were never clients because that would be highly illegal & morally
corrupt: pic.twitter.com/b17QGwxrxq
-- #NotUrFalcoLombardi (@P45K) July 6, 2015The Intercept analysed the leaked files to discover that Hacker Team's clients included the FBI, DEA, and U.S. Army, with the FBI using the software since 2011 in their 'Remote Operations Unit'.
Hacker Team's clients have been posted on an interactive world map, with an extended list of maintenance contracts signed by the company on CSOonline.
For details of the latest launches and news from Samsung, Xiaomi, Realme, OnePlus, Oppo and other companies at the Mobile World Congress in Barcelona, visit our MWC 2026 hub.
Related Stories
- Samsung Galaxy Unpacked 2026
- iPhone 17 Pro Max
- ChatGPT
- iOS 26
- Laptop Under 50000
- Smartwatch Under 10000
- Apple Vision Pro
- Oneplus 12
- OnePlus Nord CE 3 Lite 5G
- iPhone 13
- Xiaomi 14 Pro
- Oppo Find N3
- Tecno Spark Go (2023)
- Realme V30
- Best Phones Under 25000
- Samsung Galaxy S24 Series
- Cryptocurrency
- iQoo 12
- Samsung Galaxy S24 Ultra
- Giottus
- Samsung Galaxy Z Flip 5
- Apple 'Scary Fast'
- Housefull 5
- GoPro Hero 12 Black Review
- Invincible Season 2
- JioGlass
- HD Ready TV
- Latest Mobile Phones
- Compare Phones
- Realme C83 5G
- Nothing Phone 4a Pro
- Infinix Note 60 Ultra
- Nothing Phone 4a
- Honor 600 Lite
- Nubia Neo 5 GT
- Realme Narzo Power 5G
- Vivo X300 FE
- MacBook Neo
- MacBook Pro 16-Inch (M5 Max, 2026)
- Tecno Megapad 2
- Apple iPad Air 13-Inch (2026) Wi-Fi + Cellular
- Tecno Watch GT 1S
- Huawei Watch GT Runner 2
- Xiaomi QLED TV X Pro 75
- Haier H5E Series
- Asus ROG Ally
- Nintendo Switch Lite
- Haier 1.6 Ton 5 Star Inverter Split AC (HSU19G-MZAID5BN-INV)
- Haier 1.6 Ton 5 Star Inverter Split AC (HSU19G-MZAIM5BN-INV)
















