New Android Malware Forcing Users to Pay to Unlock Their Data
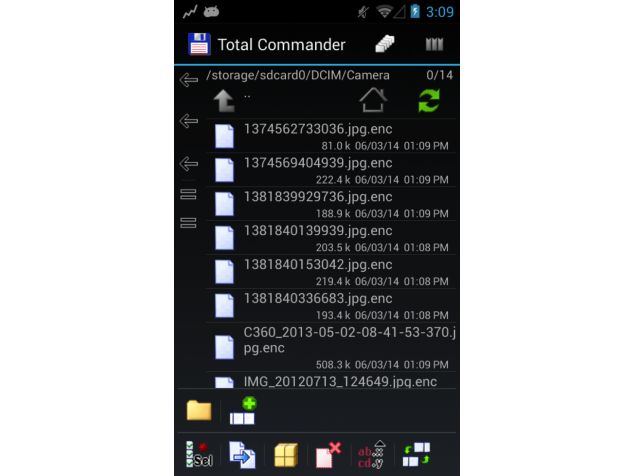
Security experts are stating that Google's Android operating system has a chance to fall prey to a Trojan malware of the ransomware variety - which encrypts photos, videos, and documents stored on the SD card of the Android device, demanding a ransom in order for them to be decrypted/ restored.
Some experts had earlier warned Internet users of a ransomware called CryptoLocker that infected a computer through social media and emails.
Just like CryptoLocker, a malicious app called Android/Simplocker is still in the proof-of-concept phase as suggested by Eset in a blog post notes Arstechnica.
Eset states that after encrypting content on the device, the app sends a random message written in Russian and asks for a ransom to be paid in Ukrainian Hryvnias. The message roughly translates to:
"WARNING your phone is locked!
The device is locked for viewing and distribution child pornography, zoophilia and other perversions.
To unlock you need to pay 260 UAH.
1. Locate the nearest payment kiosk.
2. Select MoneXy
3. Enter [REDACTED].
4. Make deposit of 260 Hryvnia, and then press pay.
Do not forget to take a receipt!
After payment your device will be unlocked within 24 hours.
In case of no PAYMENT YOU WILL LOSE ALL DATA ON your device!"
Android/Simplocker uses advanced encryption standard (AES) to encrypt files certain file extensions (jpeg, jpg, png, bmp, gif, pdf, doc, docx, txt, avi, mkv, 3gp, mp4) on the smartphone's SD card. It is still unclear if paying the ransom decrypts the data but Eset is advising affected users against it. Sophos reports the malware can be removed manually by rebooting into safe mode or by recovering the AES key stored inside the malware. The latter technique needs some technical know-how.
Get your daily dose of tech news, reviews, and insights, in under 80 characters on Gadgets 360 Turbo. Connect with fellow tech lovers on our Forum. Follow us on X, Facebook, WhatsApp, Threads and Google News for instant updates. Catch all the action on our YouTube channel.
Related Stories
- Samsung Galaxy Unpacked 2026
- iPhone 17 Pro Max
- ChatGPT
- iOS 26
- Laptop Under 50000
- Smartwatch Under 10000
- Apple Vision Pro
- Oneplus 12
- OnePlus Nord CE 3 Lite 5G
- iPhone 13
- Xiaomi 14 Pro
- Oppo Find N3
- Tecno Spark Go (2023)
- Realme V30
- Best Phones Under 25000
- Samsung Galaxy S24 Series
- Cryptocurrency
- iQoo 12
- Samsung Galaxy S24 Ultra
- Giottus
- Samsung Galaxy Z Flip 5
- Apple 'Scary Fast'
- Housefull 5
- GoPro Hero 12 Black Review
- Invincible Season 2
- JioGlass
- HD Ready TV
- Latest Mobile Phones
- Compare Phones
- Realme C83 5G
- Nothing Phone 4a Pro
- Infinix Note 60 Ultra
- Nothing Phone 4a
- Honor 600 Lite
- Nubia Neo 5 GT
- Realme Narzo Power 5G
- Vivo X300 FE
- MacBook Neo
- MacBook Pro 16-Inch (M5 Max, 2026)
- Tecno Megapad 2
- Apple iPad Air 13-Inch (2026) Wi-Fi + Cellular
- Tecno Watch GT 1S
- Huawei Watch GT Runner 2
- Xiaomi QLED TV X Pro 75
- Haier H5E Series
- Asus ROG Ally
- Nintendo Switch Lite
- Haier 1.6 Ton 5 Star Inverter Split AC (HSU19G-MZAID5BN-INV)
- Haier 1.6 Ton 5 Star Inverter Split AC (HSU19G-MZAIM5BN-INV)

















