Alleged Grindr Security Flaw Exposes Exact Location Data, Endangers Users
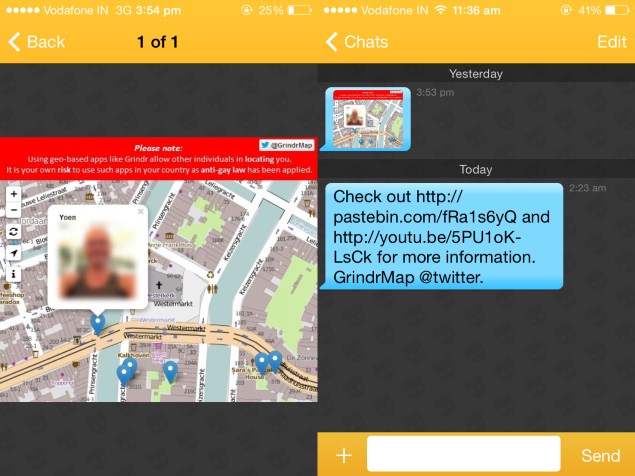
An unknown person has been sending thousands of unsolicited messages to Grindr users in countries known to be hostile to LGBT citizens, warning them of a security flaw that could allow anyone with a bit of know-how to determine their exact location. The app is widely used by gay and bisexual men to meet each other discretely, and displays profiles of its users based on proximity.
The anonymous spammer, who is presumably acting altruistically, includes links to a Twitter account, YouTube video and Pastebin text dump, which contain more information. Heor she claims to have used a secondary flaw to be able to send messages to over 100,000 users in 70 countries with anti-gay laws. The messages and posts express concern that Grindr users might be targeted, persecuted or even murdered. Homosexuality is punishable by death in several countries and violence against LGBT people and those who support them is routine and even encouraged in many places, which makes users extremely vulnerable.
According to the Pastebin dump, "officials at Grindr have been informed several times within the past months about these issues, which would seem to imply that the concept of 'social responsibility' is lost upon Grindr" (sic). "Knowing that Grindr-Users in countries such as these are being put unnecessarily at a high risk should be reason enough for Grindr to change its system," the author continues.
The location data is allegedly so accurate that someone exploiting the flaw would be able to tell "if you were using Grindr in the bathroom or on the couch". While the app only shows users the distance between them and other users, specific location data can be extrapolated by querying Grindr's servers from three different places and triangulating the information received. This process can also be automated using commonly available tools, and the resulting coordinates can be overlaid on a map.
The flaw arises from the fact that anyone can query Grindr's servers using standard JSON (JavaScript Object Notation) without needing to be authenticated. The server's response will contain whatever information users have added to their profiles, potentially including a photo, text description, age, ethnicity, body type, time last seen online, and relationship status.
Users can choose not to show their location to other users. If this flag is set, the JSON response will not contain location data. The YouTube link included in the anonymous messages and Twitter account leads to a video demonstrating the process in several parts of the world. With a single click, user profiles are displayed as pins on a map.
The second security risk is that message senders can be spoofed, and users can be impersonated. The Pastebin dump contains specific instructions including details of Grindr's messaging protocols and server addresses. This is how the unknown whistleblower has been sending out hundreds of thousands of messages.
NDTV Gadgets is in possession of screenshots of these messages which reached a user in India. The first message is a screenshot of the map in the video with a blurred profile marker, and superimposed text that reads "Using geo-based apps like Grindr allow other individuals in locating you. It is your own risk to use such apps in your country as anti-gay law has been applied." (sic). Grindr currently claims to have over five million active monthly users worldwide.
Earlier this year, a man was arrested in Lahore after murdering three men he had arranged to meet through Manjam, a similar social networking platform, in order to "send a message" about what he considered "spreading evil in society".
Get your daily dose of tech news, reviews, and insights, in under 80 characters on Gadgets 360 Turbo. Connect with fellow tech lovers on our Forum. Follow us on X, Facebook, WhatsApp, Threads and Google News for instant updates. Catch all the action on our YouTube channel.
Related Stories
- Samsung Galaxy Unpacked 2026
- iPhone 17 Pro Max
- ChatGPT
- iOS 26
- Laptop Under 50000
- Smartwatch Under 10000
- Apple Vision Pro
- Oneplus 12
- OnePlus Nord CE 3 Lite 5G
- iPhone 13
- Xiaomi 14 Pro
- Oppo Find N3
- Tecno Spark Go (2023)
- Realme V30
- Best Phones Under 25000
- Samsung Galaxy S24 Series
- Cryptocurrency
- iQoo 12
- Samsung Galaxy S24 Ultra
- Giottus
- Samsung Galaxy Z Flip 5
- Apple 'Scary Fast'
- Housefull 5
- GoPro Hero 12 Black Review
- Invincible Season 2
- JioGlass
- HD Ready TV
- Latest Mobile Phones
- Compare Phones
- Tecno Pova Curve 2 5G
- Lava Yuva Star 3
- Honor X6d
- OPPO K14x 5G
- Samsung Galaxy F70e 5G
- iQOO 15 Ultra
- OPPO A6v 5G
- OPPO A6i+ 5G
- Asus Vivobook 16 (M1605NAQ)
- Asus Vivobook 15 (2026)
- Brave Ark 2-in-1
- Black Shark Gaming Tablet
- boAt Chrome Iris
- HMD Watch P1
- Haier H5E Series
- Acerpure Nitro Z Series 100-inch QLED TV
- Asus ROG Ally
- Nintendo Switch Lite
- Haier 1.6 Ton 5 Star Inverter Split AC (HSU19G-MZAID5BN-INV)
- Haier 1.6 Ton 5 Star Inverter Split AC (HSU19G-MZAIM5BN-INV)







![[Partner Content] OPPO Reno15 Series: AI Portrait Camera, Popout and First Compact Reno](https://www.gadgets360.com/static/mobile/images/spacer.png)









